Post-Processing in Additive Manufacturing: What is it?

Simply put, additive manufacturing involves a revolutionary method of developing 3D-printed end-user sections. Additive manufacturing can be beneficial to most, ...
Read more
What Is TWS Function?

Are you curious to know what is tws function? You have come to the right place as I am going ...
Read more
Building Trust in the Era of Fake News: PR Strategies for Authenticity

In a time where people are constantly connected thanks to tiny supercomputers that they can carry in their back pocket, ...
Read more
What Is Earth Hour Amazon Quiz?

Are you curious to know what is earth hour amazon quiz? You have come to the right place as I ...
Read more
What Is Jio Fiber Service ID?

Are you curious to know what is jio fiber service id? You have come to the right place as I ...
Read more
What Is Tab Bar?
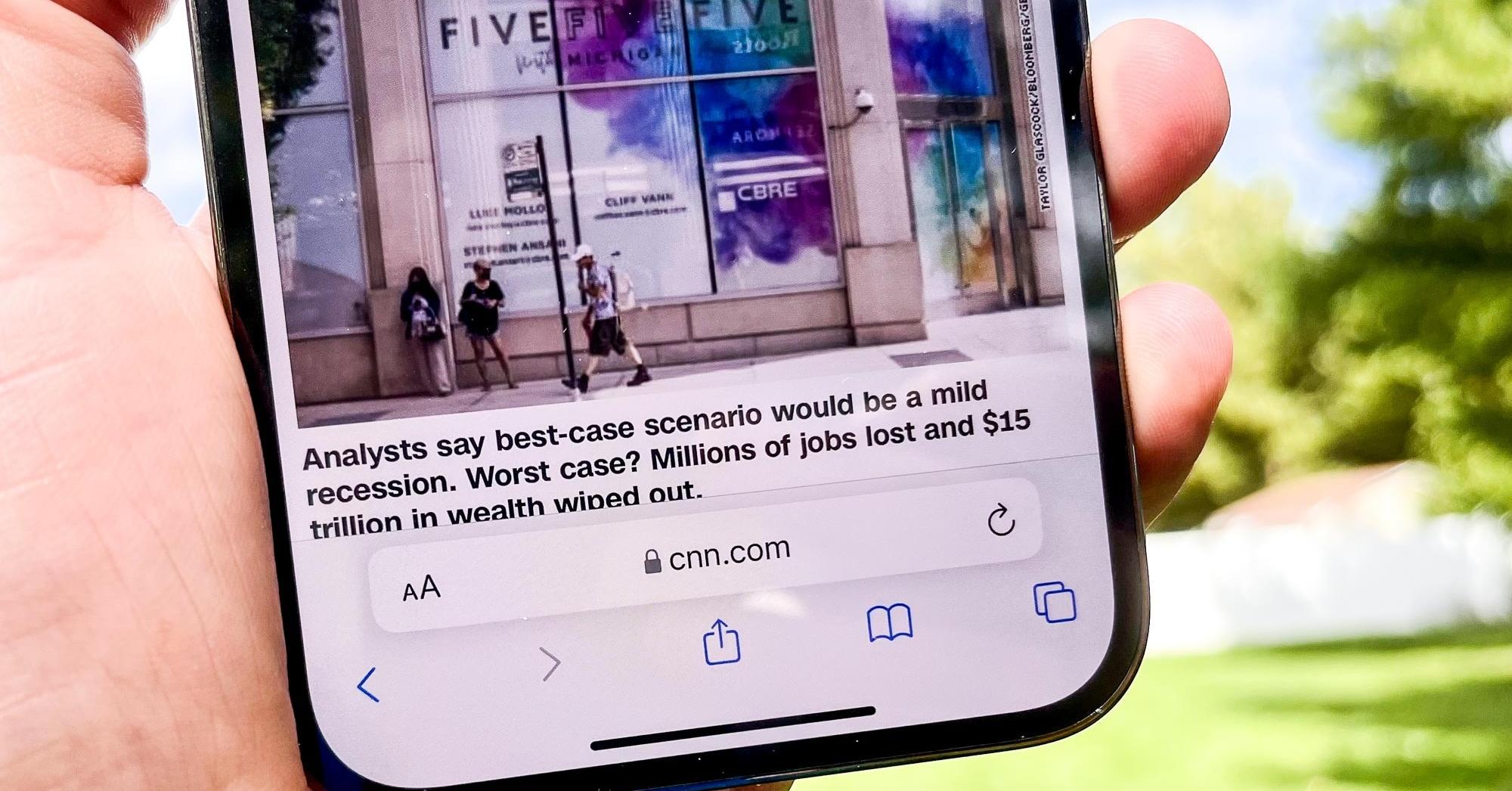
Are you curious to know what is tab bar? You have come to the right place as I am going ...
Read more
Mistakes To Avoid When Choosing A Used Laptop And Metal Scrap

Buying used laptops offers several perks that can make it an attractive option for many individuals. Some of the key ...
Read more
What Is Floating Notification?

Are you curious to know what is floating notification? You have come to the right place as I am going ...
Read more
What Is GDA?

Are you curious to know what is GDA? You have come to the right place as I am going to ...
Read more
What Is A Local Area Connection?

You may find a local area connection always seen activated in your Windows. Have you ever been curious what a ...
Read more









